In this post I am going to show you how to enable and use External Threat Feeds (ETF) on Cisco Secure Email Gateway. This feature allows you to get more detail on cybersecurity attacks from third party sources.
Cisco Secure Email Gateway (Cisco ESA) consume external threat information for the following purposes:
- Proactive response against cyber threats such as malware, ransomeware, and phishing attacks
- Subscribe to threat intelligence sources
- Improve email gateway efficacy
This communication will be established over TAXII protocol and the current version of Cisco Secure Email Gateway uses STIX format to receives watch lists. These watch lists contain the malicious activities and cyber threat information across different organisations, and provide details such as File Hashes, IPs, Domains, and URLs. External Threat Feeds (ETF) is not enabled by default on Cisco Secure Email Gateway, and enabling and using of it needs a few steps.
Requirements
Cisco Secure Email Gateway (ESA) has supported External Threat Feeds (ETF) sync AsyncOS version 12. In addition you must have the license. If you don’t know about what license do you have, you can follow the below direction to verify your licenses.
Traditional licensing model: System Administration -> License Key
Smart licensing model: System Administration -> Licenses
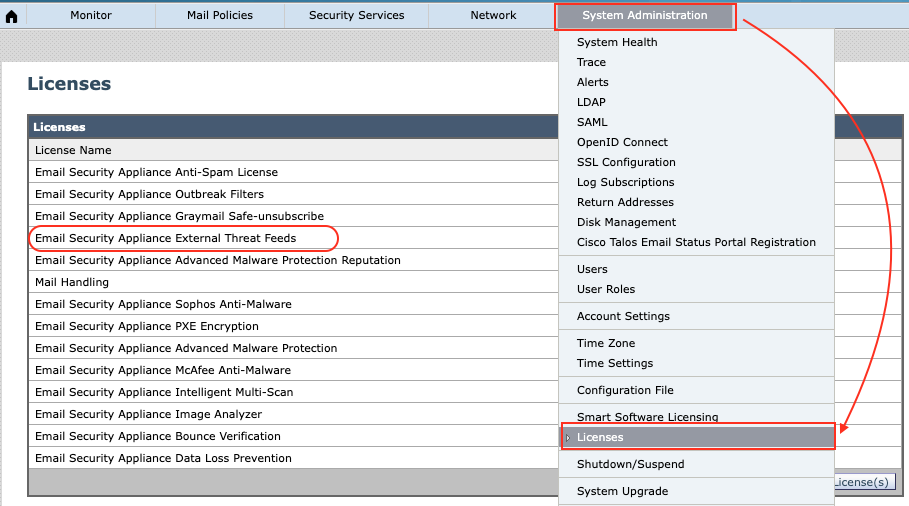
If you don’t have the External Threat Feed (ETF) license and you have at least inbound license, below procedures might be helpful to get the ETF license.
- If you are an existing user using the hardware or virtual email gateway models and you can obtain feature keys or software licenses directly from the Cisco server, you are automatically provided with an External Threat Feeds feature key.
- If you are an existing user using the virtual email gateway models and are not able to obtain feature keys or licenses directly from the Cisco server, perform the following steps to obtain an External Threat Feeds feature key:
- Log in to the License Registration Portal (LRP) using your LRP user account credentials.
- Select Get License.
- Select Migration.
- Select Security Products
- Select Email Security (ESA)
- Enter the VLN Number and generate the license file.
The generated license file includes the ETF feature. You need to install the new license file in your email gateway to use the ETF feature.
Configuring External Threat Feeds (ETF)
Enabling ETF Globally
To configure ETF, you need to enable ETF globally. To do so use the below procedure:
Services -> External Threat Feed -> Click on Enable…
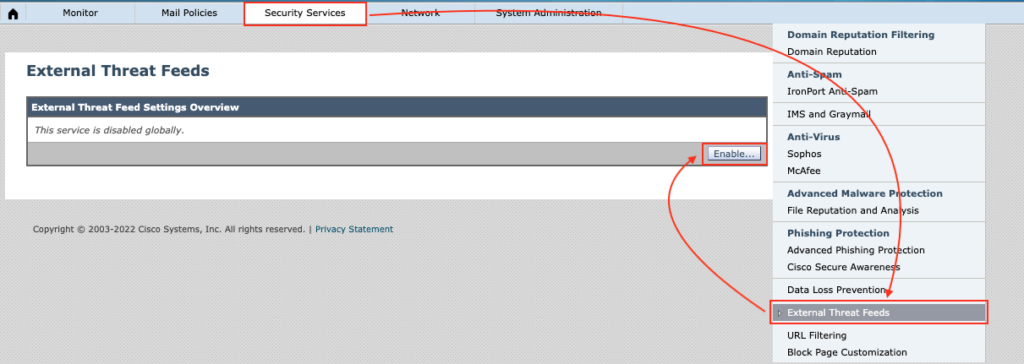
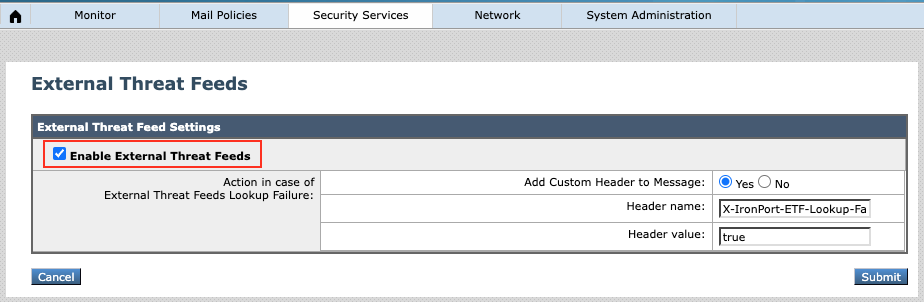
You need to accept “External Threat Feeds License Agreement”.
Then you will see the global configuration for the ETF service. The “Action in case of External Threat Feeds Lookup Failure” is an optional configuration. By enabling this feature, if ETF fails to scan the message such, ESA will add an extra header into the email headers
Adding ETF Sources
There are some open source intelligence services providing feeds over STIX protocol you can use. However in this article I use otx.alienvault.com as the ETF source. For adding a threat intelligence source into Cisco Secure Email Gateway (ESA), you should follow these steps.
Mail Policy -> External Threat Feed Manager -> Add Source
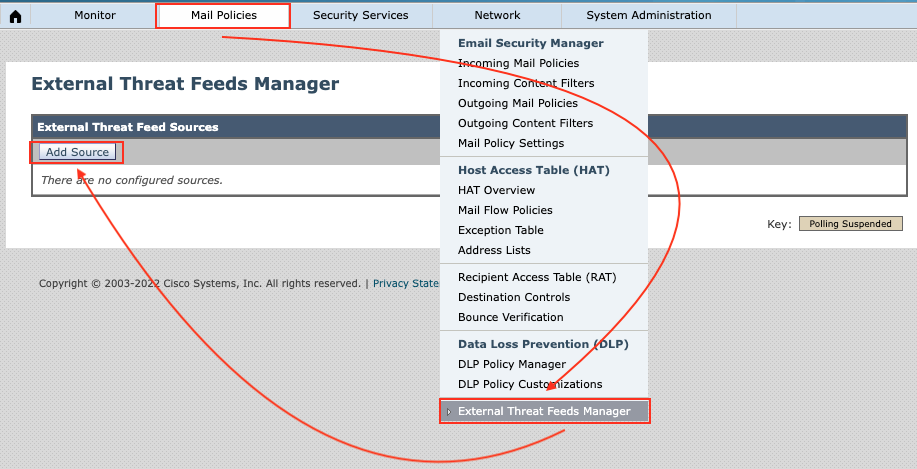
Following information are values you must provide into the Cisco Secure Email Gateway:
- Source Name: it is mandatory and you can use whatever you like.
- Description: it is an optional field
- Hostname: Provide a fully qualified domain name (FQDN) or IP address of the TAXII server. In this scenario, I used “otx.alienvault.com” server. It is an open source STIX format server, and you just need to sign up and get your OTX Key.
- Polling Path: Enter the polling service address. If you are using alienvault it is “/taxii/poll”.
- Collection Name: There might be different collection on a TAXII server, and you must specify the collection name. In my case, it is “user_AlienVault”
- Polling Interval: Enter a value to define an interval for fetching feeds from the TAXII server. The minimum value is 15 minutes and the maximum value is 24 hours. The default value is 60 Minutes and it is a proper time for most case scenarios
- Age of Threat Feeds: This is the value of feeds’ age. You can limit your Cisco Secure Email Gateway (ESA) to avoid download old feeds. The age value can be between one through 365 days.
- Time Span of Poll Segment:
- Use HTTPS: If your TAXII server working over HTTPS select yes.
- Configure User Credentials: TAXII servers might be protected by credentials, and for authentication purpose you need username and password. In the otx.alenvault.com scenario, you must use the OTX key.
- Proxy Details: Optionally if your Cisco Secure Email gateway (ESA) use a proxy for communicating to the Internet, enable this option.
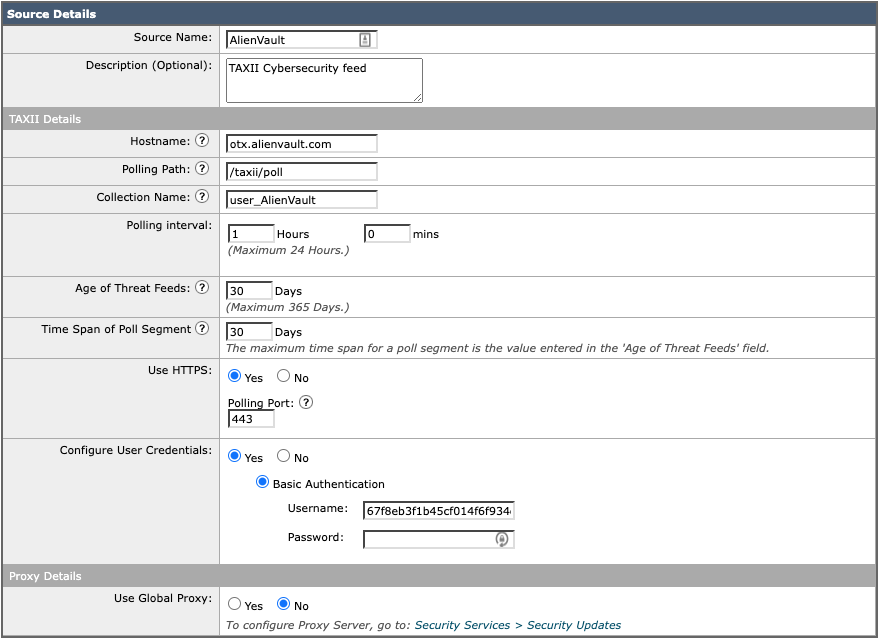
Note**: Cisco Secure Email gateway (ESA) is capable to connect up to 8 External Threat Feeds (ETF) server.
Using ETF in Policies
There are two spots that you can use ETF on Cisco Secure Email Gateway (ESA):
- Mail Policies (HAT)
- Content Filters
- Message Filters
ETF on Mail Policies (HAT)
The below steps guid you how to enable ETF on incoming mail policies.
Mail Policies -> Host Access Table (HAT) -> HAT Overview -> Click on Desired Sender Group -> Click on Edit Settings… -> in the External Feeds part choose desired feed source
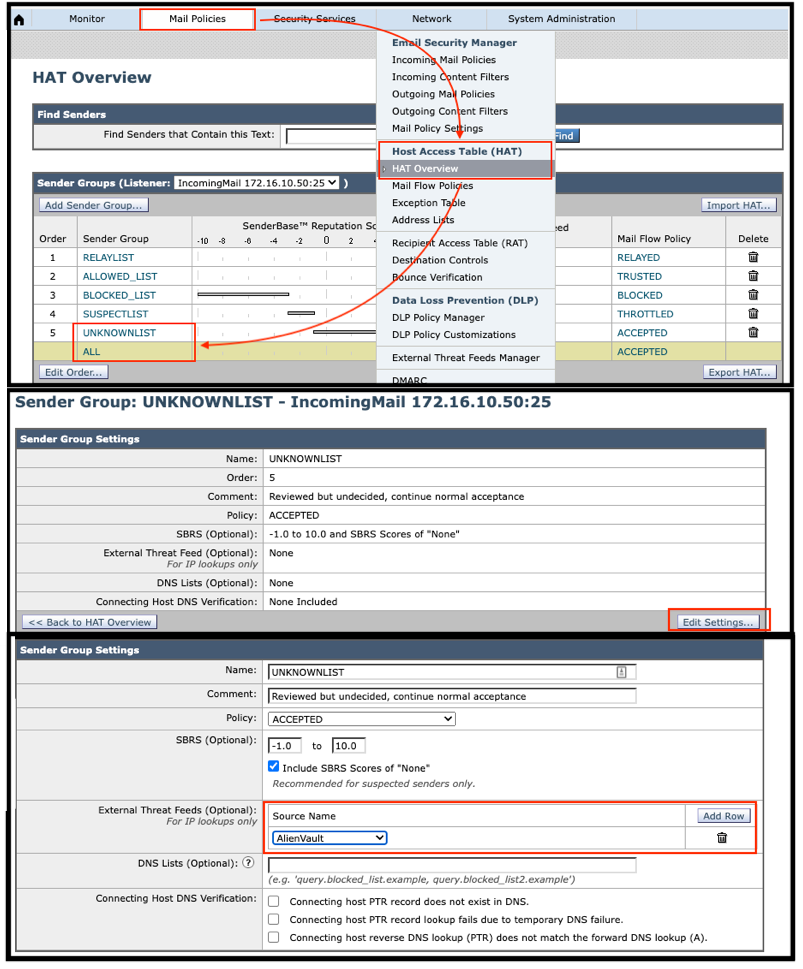
Note:
- f you are using default HAT, adding ETF for UNKNOWN and ALL sender groups is suggested.
- External Threat Feed provides different cyber activities information, but HAT uses ETF only for IP Lookups
- If you have more that one ETF source, you can add others by clicking on
Content Filters
Unlike HAT, in Content Filters we can use External Threat Feed to detection malicious domain, malicious URL, and malicious file. To do so, you can follow the below procedure.
Mail Policies -> Incoming Content Filter -> Add Filter… -> provide proper name (Mandatory) and description (Optional)-> click on Add Condition …
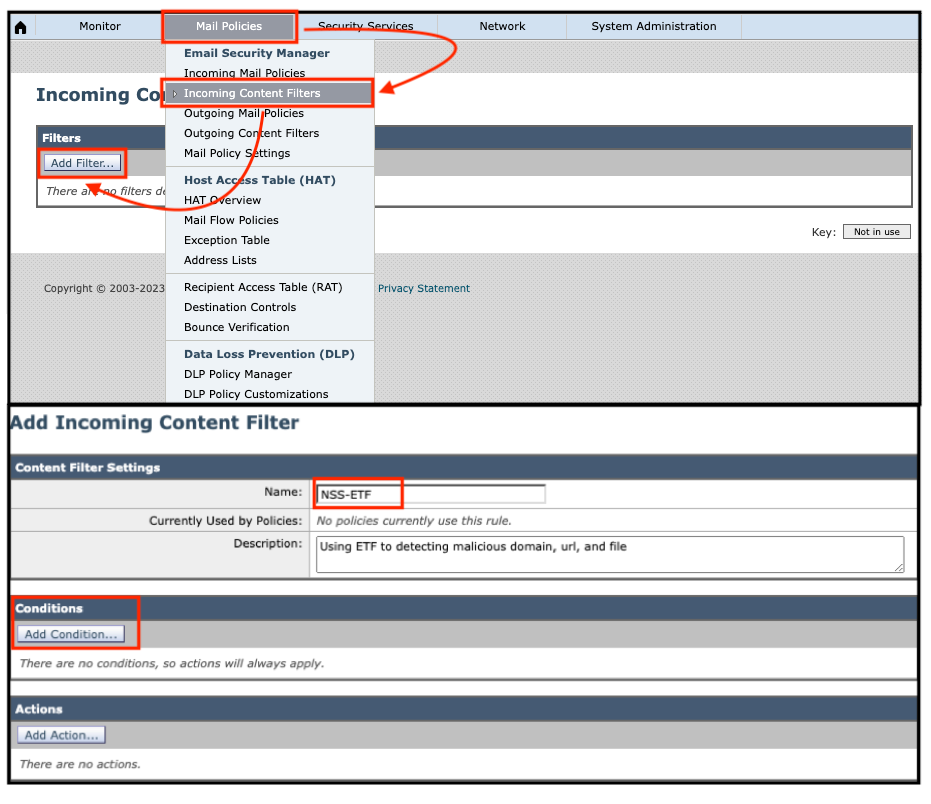
Malicious Domains
For detecting malicious domains, choose Domain Reputation -> select External Threat Feeds -> add available sources
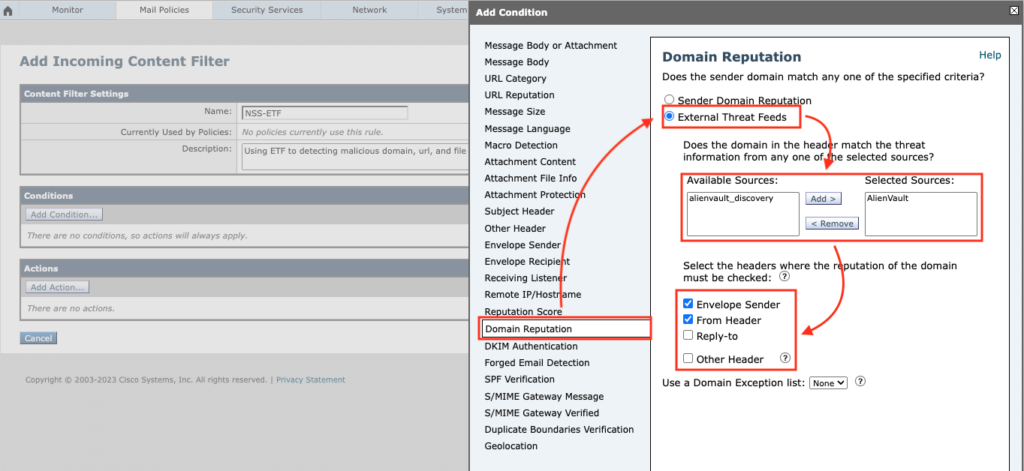
Make sure that you have select the header(s) that you want to ETF evaluates domain name inside of them. In addition, you have optional choice to except domains by using Domain Exception List.
Malicious URLs
For detecting malicious urls, select URL Reputation -> select External Threat Feeds -> add available sources
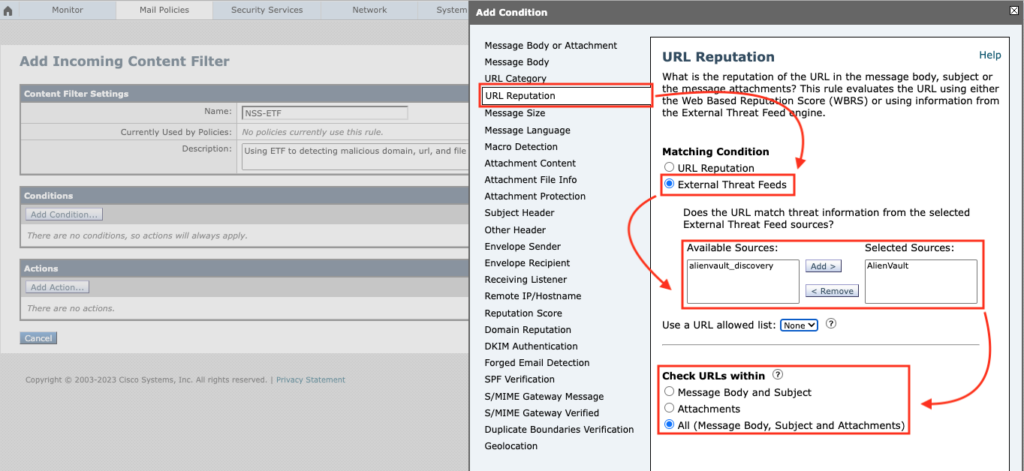
You can tell Cisco ESA to check which part of message to looking for malicious URL (Message body, Subject, Attachment, or All parts). In addition, you have optional choice to except URL by using URL Allow List.
Malicious Files
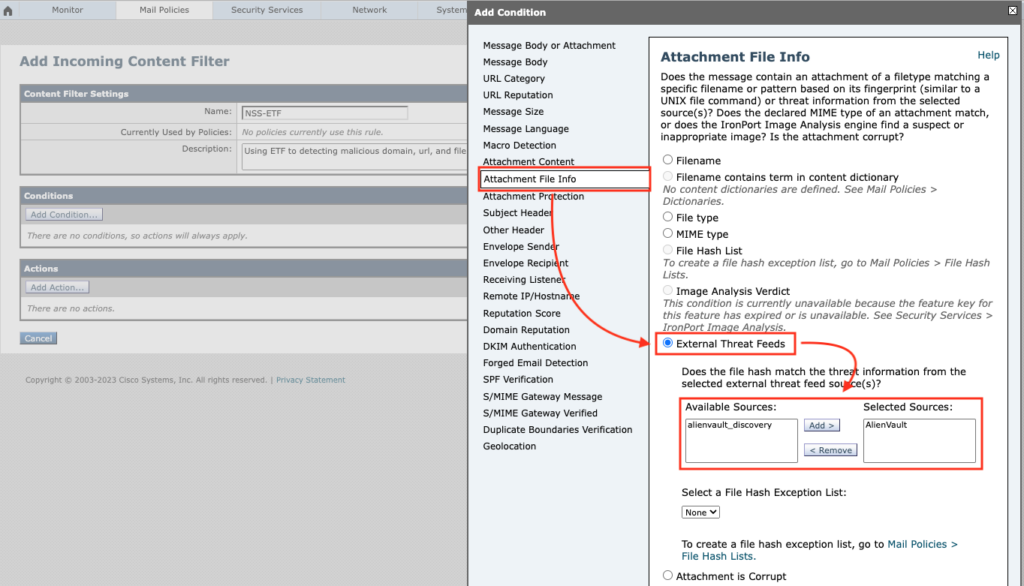
For detecting malicious files, select Attachment File Info -> select External Threat Feeds -> add available sources
You have optional choice to except specific files by using File Hash Exception List.
Conclusion
Having multiple Threat Intelligence sources for evaluating messages against Cyber Threats will bring you additional security layer along with good experience for endusers due to they receive less spam or any other unwanted emails.